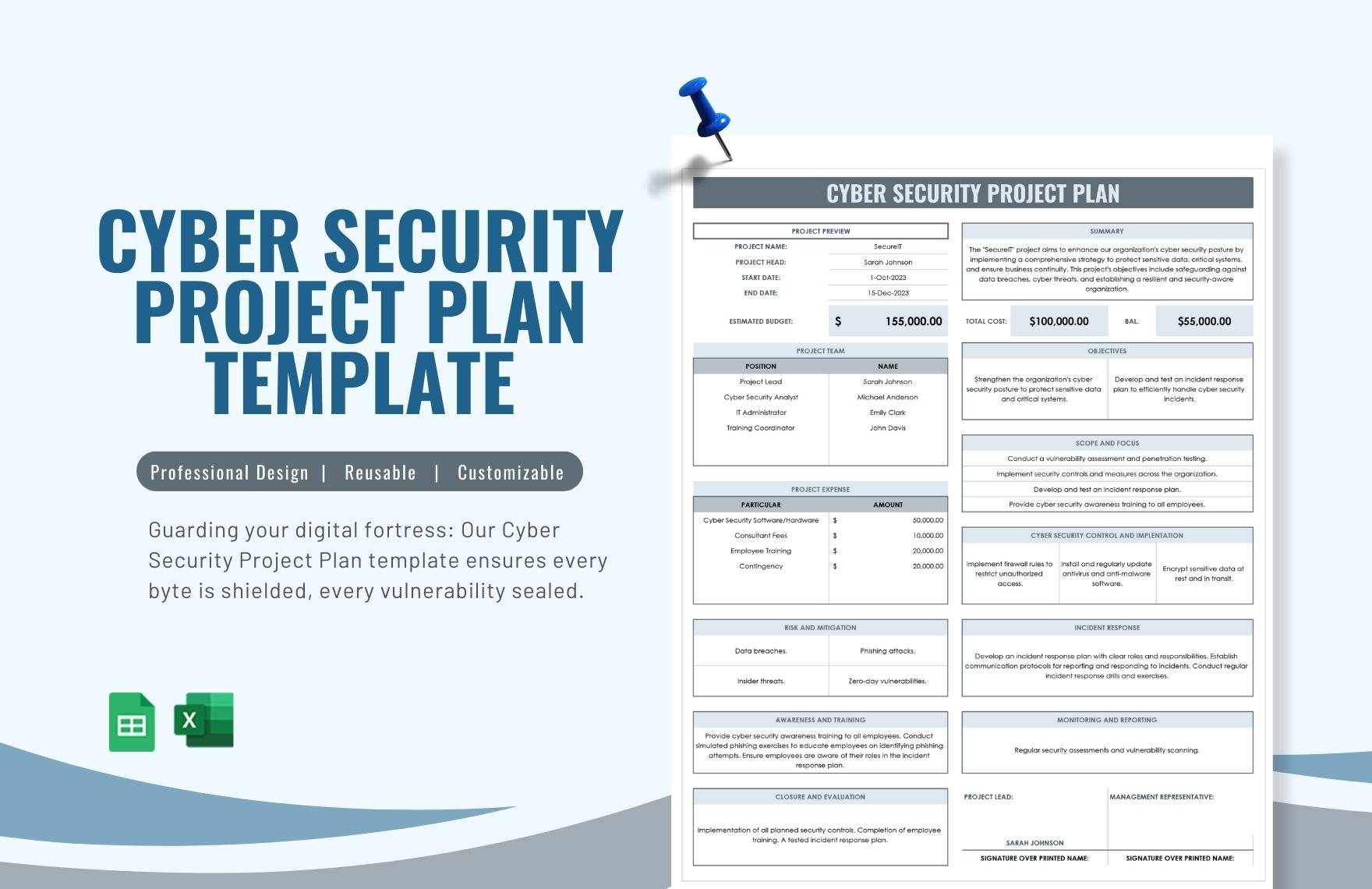
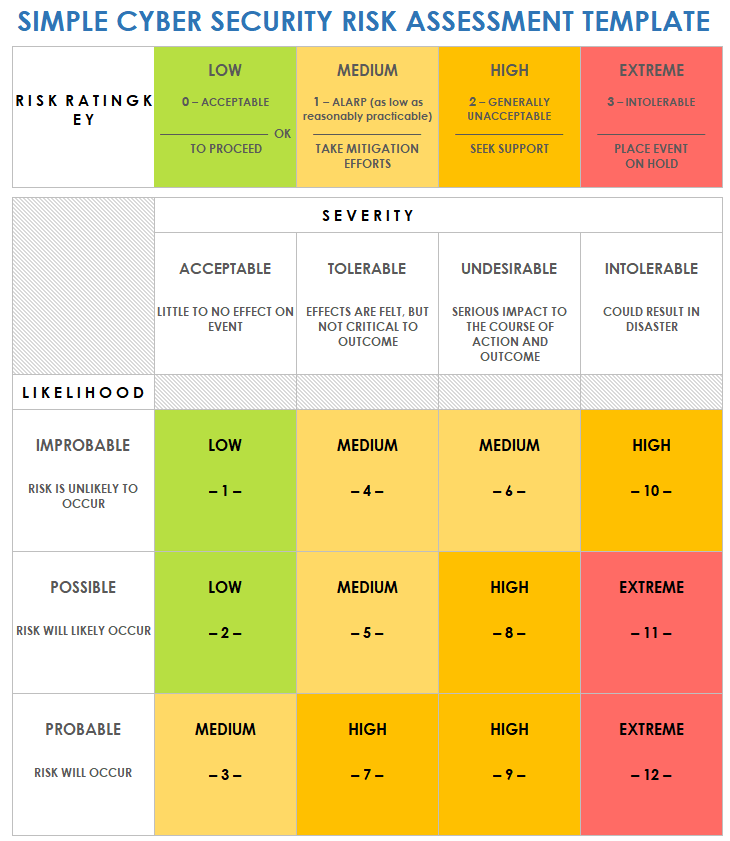
Cyber Security Plan Template - Ongoing monitoring and assessment activities will commence, as described in section 4.4,. Use this tool to create and save a custom cyber security plan for your company, choosing from. The policy templates are provided courtesy of the state of new york and the state of california. Learn how to protect your data, privacy and business from cyber threats with this.
The policy templates are provided courtesy of the state of new york and the state of california. Ongoing monitoring and assessment activities will commence, as described in section 4.4,. Use this tool to create and save a custom cyber security plan for your company, choosing from. Learn how to protect your data, privacy and business from cyber threats with this.
Learn how to protect your data, privacy and business from cyber threats with this. The policy templates are provided courtesy of the state of new york and the state of california. Use this tool to create and save a custom cyber security plan for your company, choosing from. Ongoing monitoring and assessment activities will commence, as described in section 4.4,.
Cybersecurity Strategy Template
The policy templates are provided courtesy of the state of new york and the state of california. Use this tool to create and save a custom cyber security plan for your company, choosing from. Ongoing monitoring and assessment activities will commence, as described in section 4.4,. Learn how to protect your data, privacy and business from cyber threats with this.
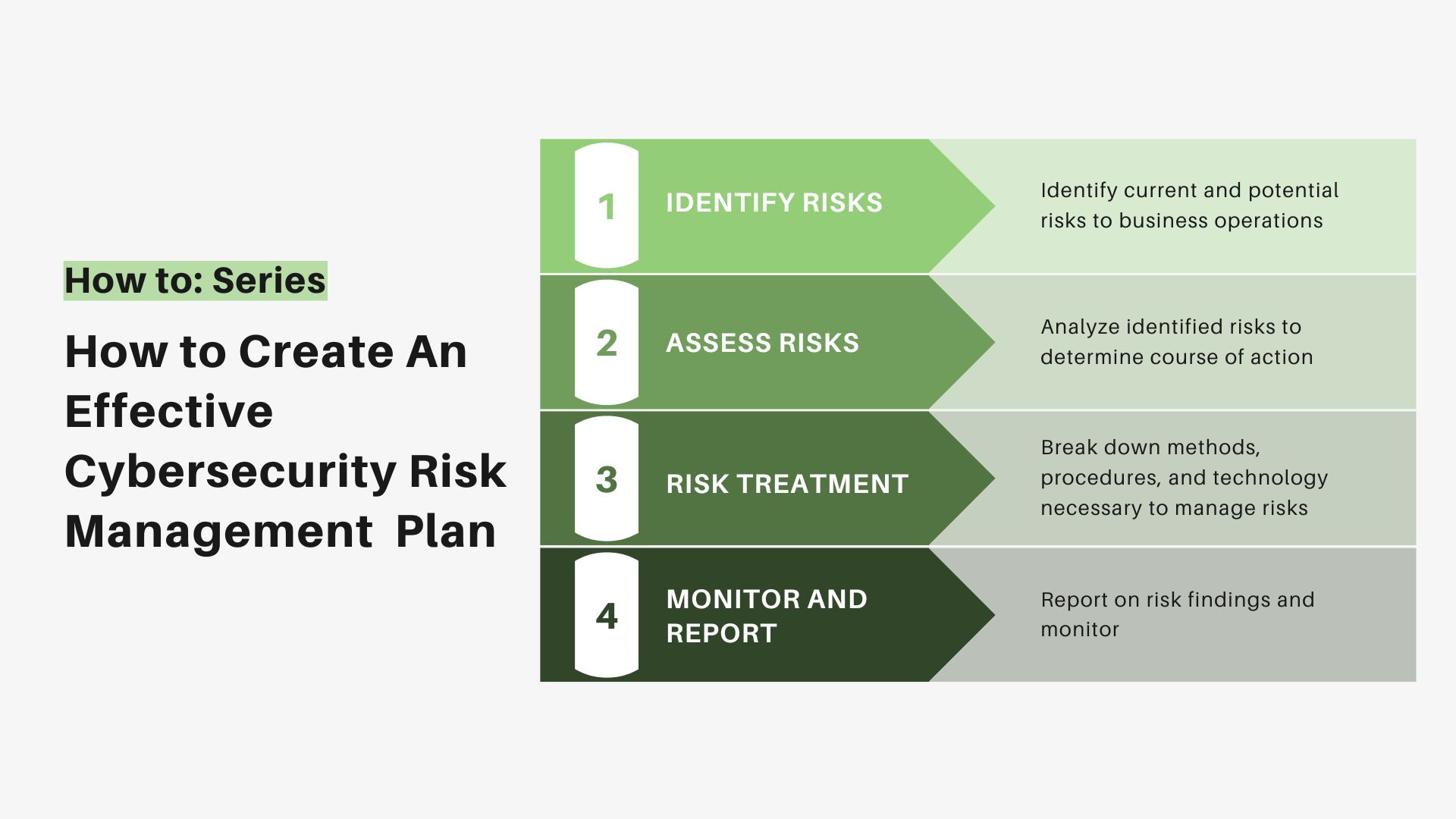
How to Create an Effective Cybersecurity Risk Management Plan TitanFile
Learn how to protect your data, privacy and business from cyber threats with this. Ongoing monitoring and assessment activities will commence, as described in section 4.4,. The policy templates are provided courtesy of the state of new york and the state of california. Use this tool to create and save a custom cyber security plan for your company, choosing from.
Cyber Security Policy Template Easy Legal Templates
Use this tool to create and save a custom cyber security plan for your company, choosing from. Ongoing monitoring and assessment activities will commence, as described in section 4.4,. The policy templates are provided courtesy of the state of new york and the state of california. Learn how to protect your data, privacy and business from cyber threats with this.
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab
Learn how to protect your data, privacy and business from cyber threats with this. The policy templates are provided courtesy of the state of new york and the state of california. Ongoing monitoring and assessment activities will commence, as described in section 4.4,. Use this tool to create and save a custom cyber security plan for your company, choosing from.
Cyber Security Implementation Plan Template
Use this tool to create and save a custom cyber security plan for your company, choosing from. Ongoing monitoring and assessment activities will commence, as described in section 4.4,. Learn how to protect your data, privacy and business from cyber threats with this. The policy templates are provided courtesy of the state of new york and the state of california.
Cyber Security Policy template Real World Help Centre
The policy templates are provided courtesy of the state of new york and the state of california. Ongoing monitoring and assessment activities will commence, as described in section 4.4,. Learn how to protect your data, privacy and business from cyber threats with this. Use this tool to create and save a custom cyber security plan for your company, choosing from.
42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab
Use this tool to create and save a custom cyber security plan for your company, choosing from. The policy templates are provided courtesy of the state of new york and the state of california. Learn how to protect your data, privacy and business from cyber threats with this. Ongoing monitoring and assessment activities will commence, as described in section 4.4,.
FREE Cyber Security Templates Download in Word, Google Docs, Excel
Ongoing monitoring and assessment activities will commence, as described in section 4.4,. Use this tool to create and save a custom cyber security plan for your company, choosing from. Learn how to protect your data, privacy and business from cyber threats with this. The policy templates are provided courtesy of the state of new york and the state of california.
Free Cybersecurity Risk Assessment Templates Smartsheet
Use this tool to create and save a custom cyber security plan for your company, choosing from. Ongoing monitoring and assessment activities will commence, as described in section 4.4,. The policy templates are provided courtesy of the state of new york and the state of california. Learn how to protect your data, privacy and business from cyber threats with this.
Cyber Security Policy Template
Use this tool to create and save a custom cyber security plan for your company, choosing from. The policy templates are provided courtesy of the state of new york and the state of california. Ongoing monitoring and assessment activities will commence, as described in section 4.4,. Learn how to protect your data, privacy and business from cyber threats with this.
Use This Tool To Create And Save A Custom Cyber Security Plan For Your Company, Choosing From.
Learn how to protect your data, privacy and business from cyber threats with this. The policy templates are provided courtesy of the state of new york and the state of california. Ongoing monitoring and assessment activities will commence, as described in section 4.4,.
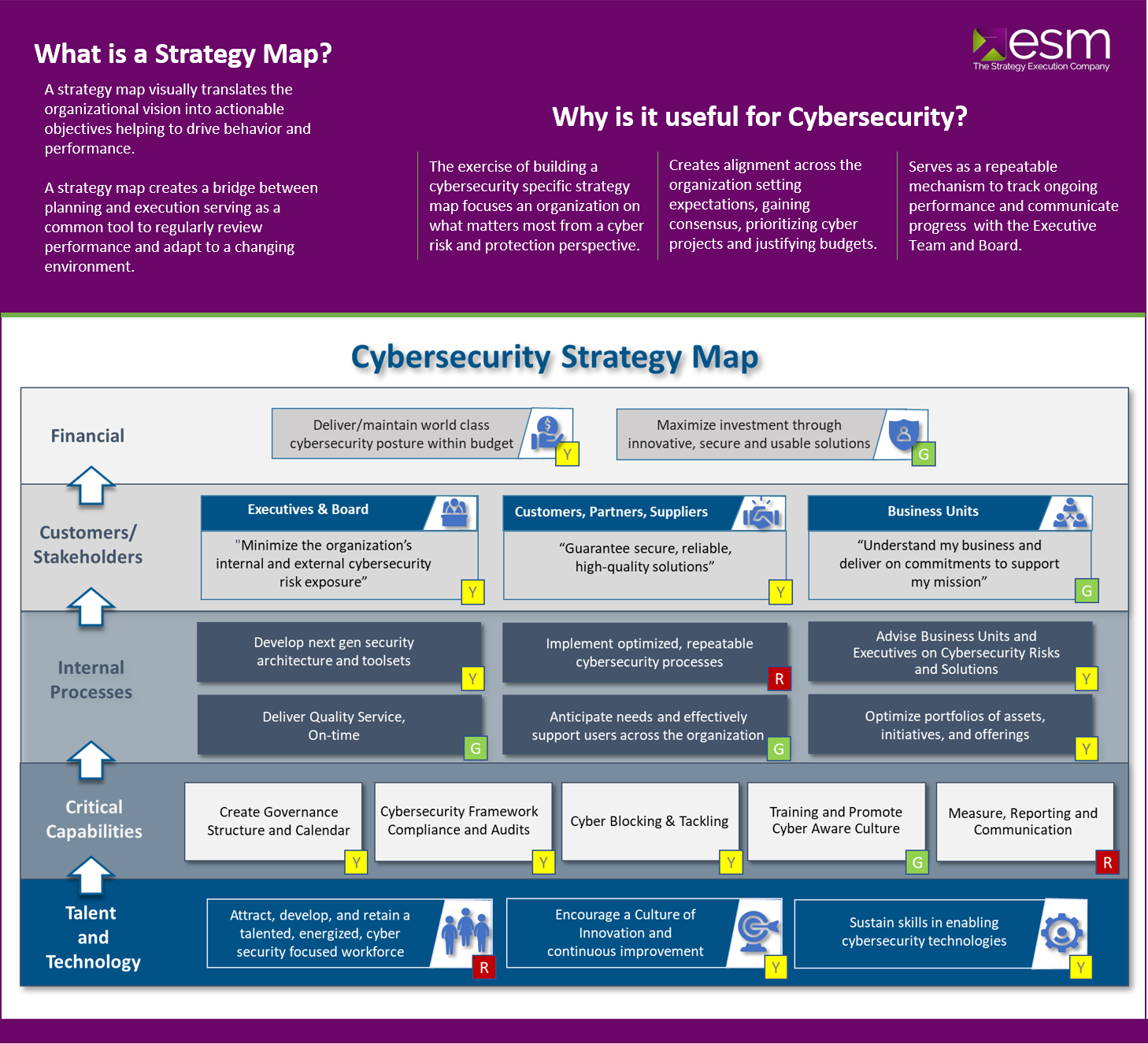

![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-06.jpg)

![42 Information Security Policy Templates [Cyber Security] ᐅ TemplateLab](https://templatelab.com/wp-content/uploads/2018/05/Security-Policy-03.jpg)